What is User Activity Monitoring (UAM)
-
Kate Borucka
- October 8, 2024
- 14 min read

Content updated on 8.10.2024
Monitoring user activity is considered controversial by many. Although this practice becomes more and more popular in the business world, it’s often associated with invading employee privacy and crossing trust boundaries.
From 2020 to 2021 (during the pandemic,) TimeCamp experienced a 28% increase in registered users.
While nobody likes to be the subject of surveillance, user activity tracking can bring many benefits. (Yes, it can!) Especially if your business is struggling, either with efficiency, employee retention, time management, financial management, or finding customers.
User activity monitoring software can help you solve many business challenges.
Here’s everything you need to know about user activity monitoring, how it can help your business, and how to monitor user activity wisely in your company.
Definition of User Activity Monitoring (UAM)
User Activity Monitoring (UAM) is a process that involves tracking, recording, and analyzing the activities of users within an organization’s digital environment. This includes monitoring behaviors across various systems, networks, applications, and devices.
It’s about keeping an eye on what’s happening behind the scenes to gain insights into how users interact with the technology. UAM can encompass everything from tracking keystrokes and mouse movements to monitoring network usage, file access, and software interactions.
User activity monitoring isn’t about watching over your employee’s shoulders—it’s about understanding their interactions and how it can help them work better.
Workplace monitoring has advanced from basic time-tracking to sophisticated digital surveillance, evolving with technology. The shift to digital workplaces, especially post-2000s, required new methods like user activity monitoring to track digital actions, protect data, and support remote work.
Get to know where your time goes with TimeCamp!
Track time in projects and tasks, create reports, and bill your clients in just one tool.
The Difference Between User Activity Monitoring and Employee Monitoring
While user activity monitoring shares some similarities with other types of monitoring, like employee monitoring or network monitoring, it’s a bit of a jack-of-all-trades.
Employee monitoring usually focuses on tracking productivity and work habits, while network monitoring is all about the flow of data across an organization’s network. User activity monitoring, on the other hand, covers a broader range, blending these elements and more to give a full picture of user activities.
Why Is User Activity Monitoring Important?
The Hawthorne effect refers to the increase in the performance of individuals who are noticed, watched, and paid attention to by researchers or supervisors. — Simply Psychology
User activity monitoring serves multiple purposes: enhancing security, ensuring compliance, improving productivity, and providing valuable data for decision-making.
Monitoring user activity is important as it helps to strengthen and grow a company. Since it’s applicable in many areas, it helps to secure business in many ways:
- Monitoring user behavior analytics helps to make smarter decisions and optimize resource utilization.
- It helps to detect and mitigate potential insider threats and suspicious activity.
- Allows you to spot bottlenecks and areas for improvement.
- Helps to set and measure KPIs that are adequate to your business endeavors.
- User activity monitoring software helps employees to work on their efficiency and understand how they spend their work hours.
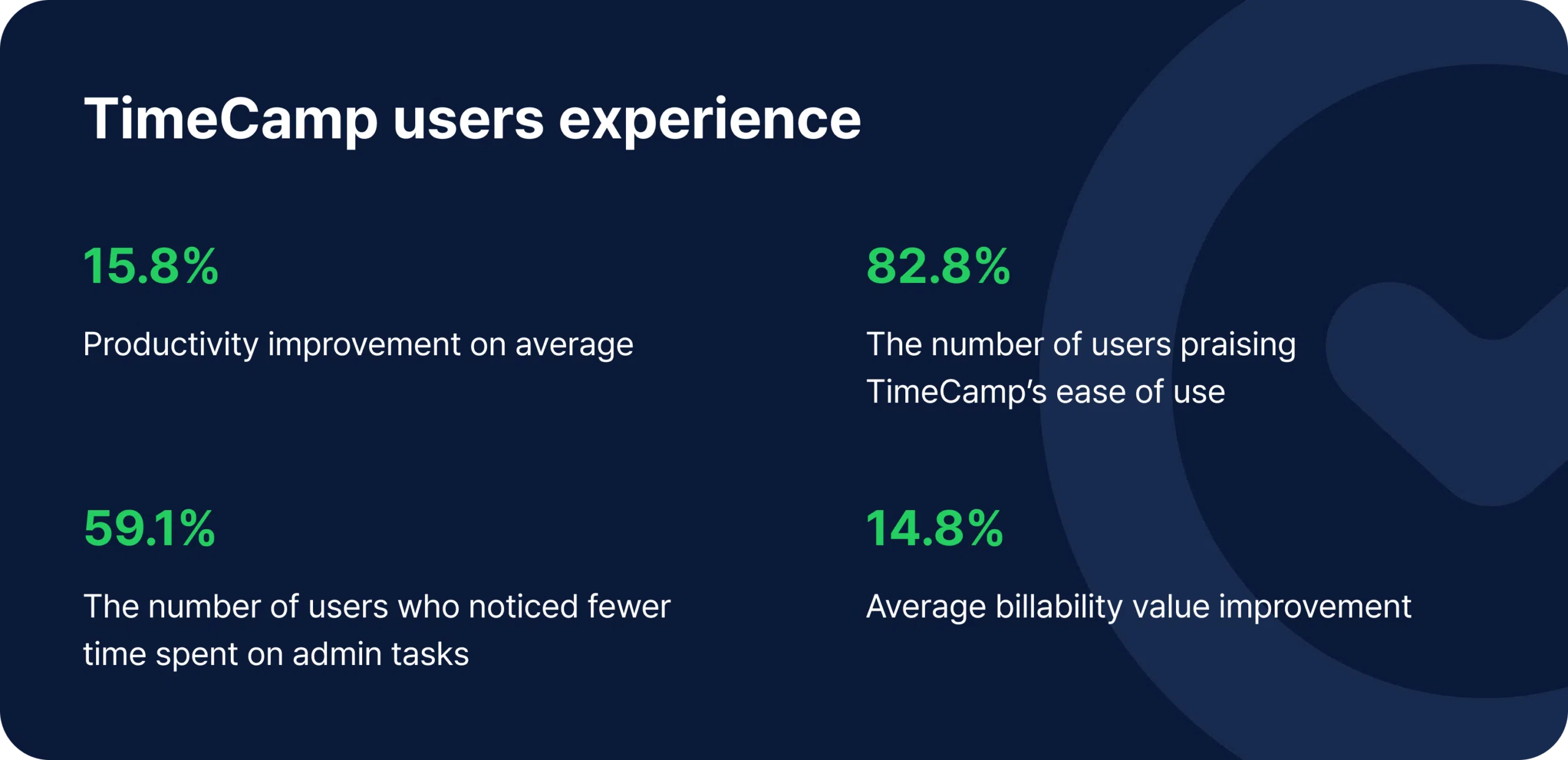
Three quarters of TimeCamp’s users track their time primarily for project performance analytics or to ensure accurate billing, but only a fifth of the users admit they use time tracking mainly to monitor the activities of their employees. This suggests that employers’ motivation for using time tracking apps is largely driven by business performance improvement, rather than staff surveillance per se.
Even if an employer admits that monitoring employees is the main reason for using TimeCamp, it does not support any claims of malicious intent against their staff. Their motives might be driven by the need to distribute work evenly among team members based on everyone’s available capacity, for example.

In today’s digital-first world, where remote work, cybersecurity threats, and compliance regulations are increasingly prevalent, user activity monitoring tools are of great help in keeping your business secure and profitable.
How User Activity Monitoring Works
While user activity monitoring is associated with surveillance and micromanagement, it’s actually a very specific process based on 3 main elements:
1) Basic Principles and Mechanisms
UAM operates on the principle of continuous observation and data collection. It uses dedicated user activity monitoring solutions installed on devices or within networks to track user actions, such as logging in and out, accessing files, sending emails, or using applications.
This data is then transmitted to a central server where it can be analyzed and reported.
In this context, TimeCamp helps businesses spot inefficiencies within their organization. They can later use these insights to tweak their workflow, provide productivity coaching to employees, or analyze how well their past projects went.
UAM systems are often designed to flag unusual or unauthorized activities (e.g., suspicious user activity, unauthorized access attempts), triggering alerts for further investigation.
TimeCamp can automatically track apps used, websites visited, and files opened if a company wishes to do so. Businesses do this to discourage employees from accessing restricted content or using unauthorized software. All it takes is downloading and installing TimeCamp’s desktop app and letting it run in the background.
When we’re talking about less intrusive forms of monitoring employee activity—time tracking, for example, it simply collects your data in a cloud-based platform for further use and analysis.
2) Tools and Software Used in UAM
There are numerous user activity monitoring software and tools available, ranging from basic monitoring tools to advanced platforms integrated with artificial intelligence (AI) and machine learning (ML).
These tools offer a range of user activity monitoring features such as real-time monitoring, automated alerts, detailed reporting, and integration with other security systems.
TimeCamp is one such software, and it belongs in the time tracking and activity tracking categories. We offer reports that show the structure of each day, work hours, tasks completed, etc. Businesses often refer to these reports days, weeks, or months after a job is done to gauge how well they performed compared to their initial expectations.
3) Key Metrics Tracked
UAM systems track a wide array of metrics depending on the organization’s needs. Common metrics include:
- Keystrokes: Recording every key pressed by the user.
- Application usage: Tracking which applications are used, for how long, and what actions are performed within them.
- File access: Monitoring access to sensitive files and data.
- Web activity: Recording websites visited, duration of visits, and actions taken.
- Email and communication: Monitoring email content and communication patterns.
- System events: Logging system-level events like logins, logouts, and device connections.
All these metrics are meant to track user activity and monitor user behavior for analytical purposes as they help in improving business efficiency.
Get to know where your time goes with TimeCamp!
Track time in projects and tasks, create reports, and bill your clients in just one tool.
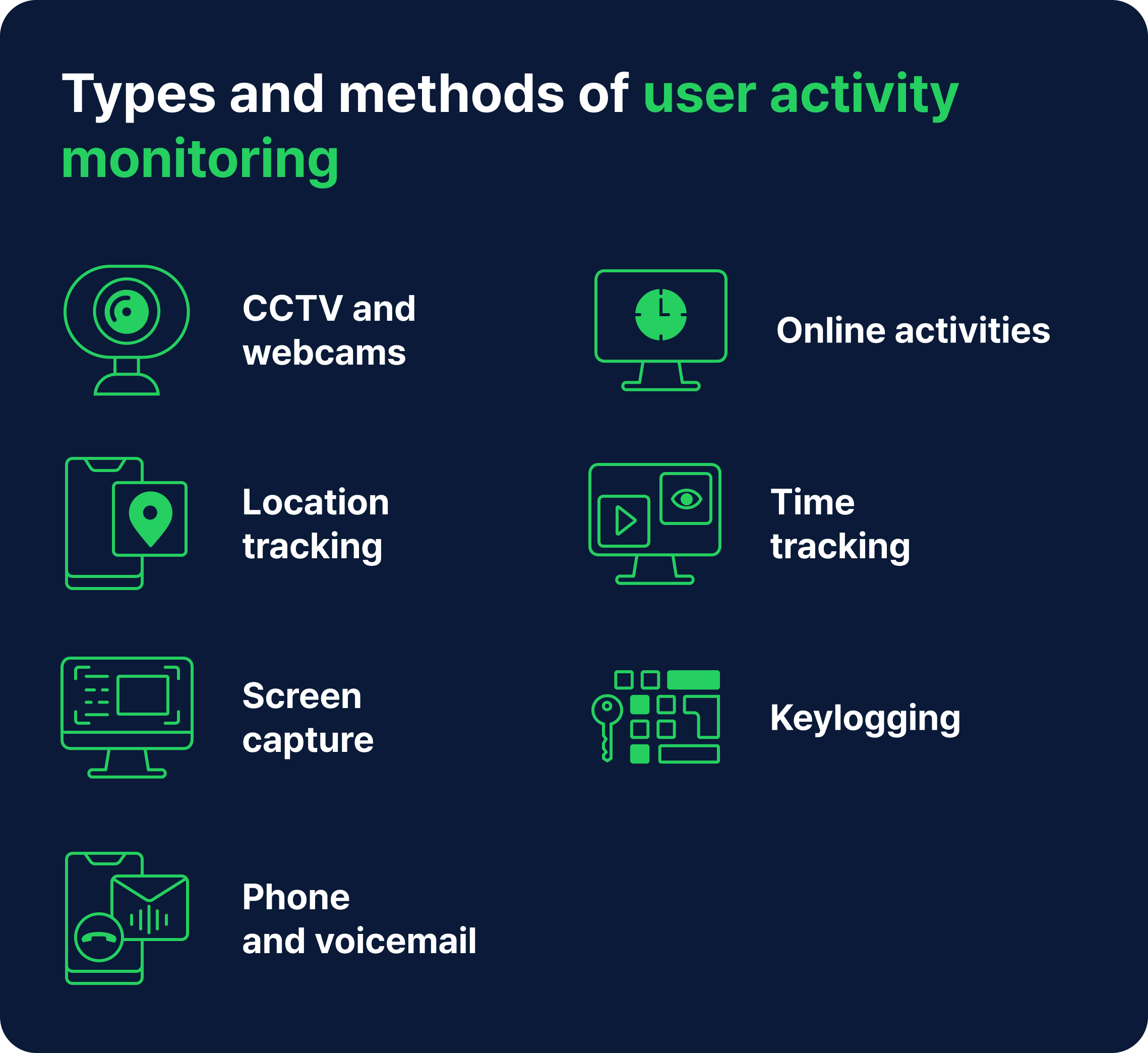
Types of User Activity Monitoring
Take a look at the different types of employee activity tracking and how they can help you improve business processes.
Real-Time Monitoring
Real-time monitoring involves the continuous tracking of user activities as they happen. This type of monitoring usually works in two ways:
-
Monitoring user activities to identify and respond to potential security threats immediately (e.g., if an employee attempts to access a restricted file or sends sensitive information outside the company, real-time monitoring can trigger an alert, allowing security teams to intervene before any damage is done).
-
Tracking user activity to monitor work progress, distribute resources wisely, and better plan work.
The primary benefit of real-time monitoring is its immediacy. It provides an easy way to view how work progresses. And as a security measure, it helps to maintain data security and quickly act on insider threat detection.
However, real-time monitoring can be perceived as invasive by employees, which could impact morale and trust.
Passive Monitoring
Passive monitoring, unlike real-time monitoring, involves the collection of user activity data for later analysis. This type of monitoring is often used for compliance purposes, to review employee productivity, or to conduct analysis after an incident has occurred.
It’s less intrusive and can be more user-friendly to employees, as it does not involve continuous observation.
Passive monitoring allows organizations to collect and analyze data at their own pace, which can be particularly useful for long-term trend analysis and performance reviews. However, the downside is that it does not offer immediate threat detection, which means that any malicious activity could go unnoticed until the data is reviewed.
Network Monitoring
Network monitoring focuses on observing the flow of data across an organization’s network. This includes tracking data packets, monitoring bandwidth usage, and identifying unusual network activity—everything related to the network usage.
Network monitoring provides insights into how users interact with network resources, such as accessing files on a shared drive or communicating over the company’s intranet.
Network monitoring systems are often integrated with user activity monitoring tools to provide a more comprehensive view of user activities.
Endpoint Monitoring
Fun fact: Most machines in factories and critical public infrastructure are not connected to any external network at all for security reasons. This greatly reduces risk of disrupting a national grid system or a hospital by malicious actors.
Endpoint monitoring involves tracking activities on individual devices. By monitoring endpoints, organizations can detect unauthorized software installations, monitor data access, and ensure that devices are compliant with security policies.
Commonly monitored endpoints include:
- Desktops and laptops: Monitoring application usage, system changes, and data access.
- Mobile devices: Tracking location, application usage, and communication.
- Servers: Monitoring user access, system performance, and data transfers.
- IoT devices: Tracking usage and security status of connected devices.
Benefits of User Activity Monitoring
Seemingly invasive employee monitoring software and user activity monitoring software can help your business. If implemented in a smart way, your business and employees won’t experience any negative outcomes.
Take a look at all the user activity monitoring benefits:
1. Enhanced Security
One of the most significant benefits of user activity monitoring is its ability to detect insider threats. These threats can come from employees, contractors, or business partners who have access to sensitive information.
A good user activity monitoring solution can help identify unusual patterns of behavior, such as attempts to access restricted areas of the network or downloading large amounts of data, which could indicate malicious intent.
By catching these activities early, you can mitigate the risk of data breaches, intellectual property theft, and other security incidents.
UAM software plays a crucial role in protecting sensitive data by monitoring how it is accessed, used, and transferred within the organization. This level of oversight helps prevent unauthorized access and ensures that data is handled in compliance with security policies.
2. Improved Productivity
User monitoring software provides detailed insights into how employees spend their time, which can be used to optimize workflows and improve productivity. By analyzing data on application usage, time spent on tasks, and overall work patterns, you can identify bottlenecks, inefficiencies, and opportunities for improvement.
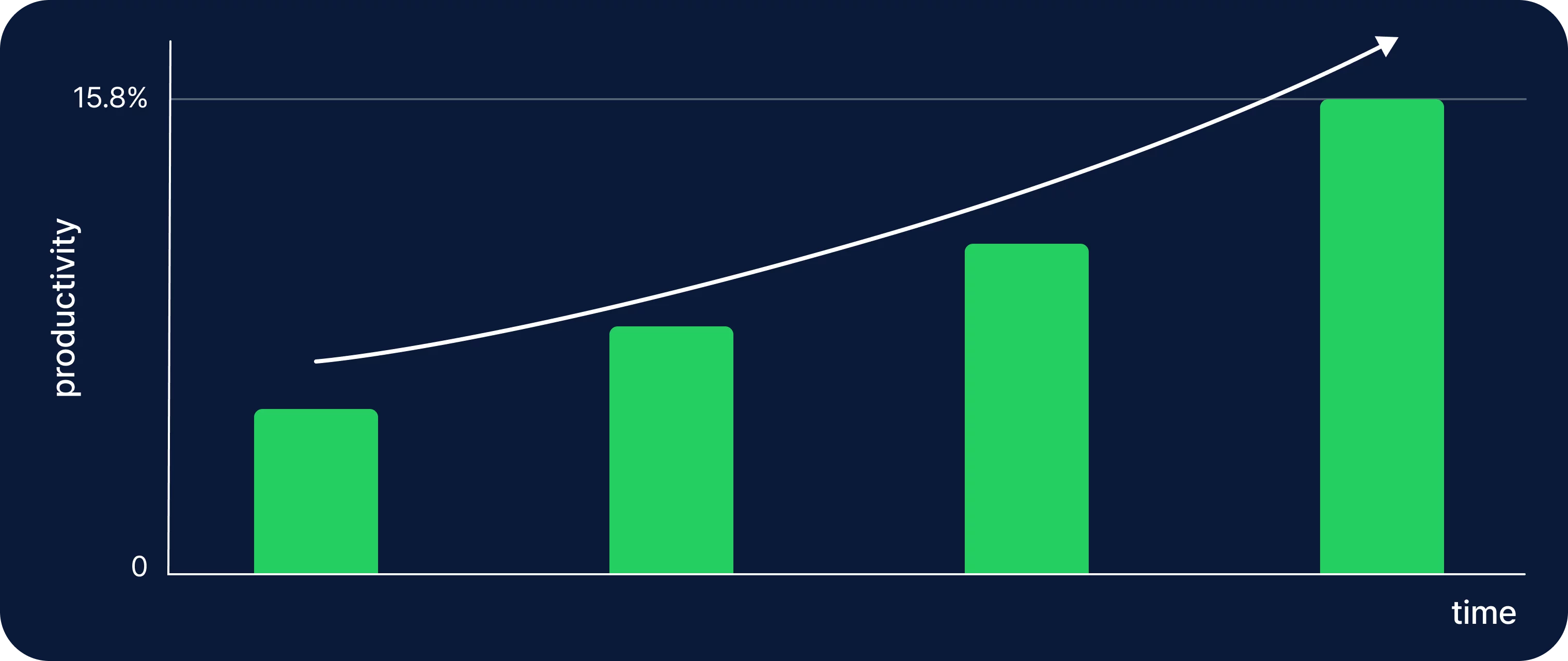
You can find all these features in TimeCamp—a time tracking software that works as an automatic user tracking system.
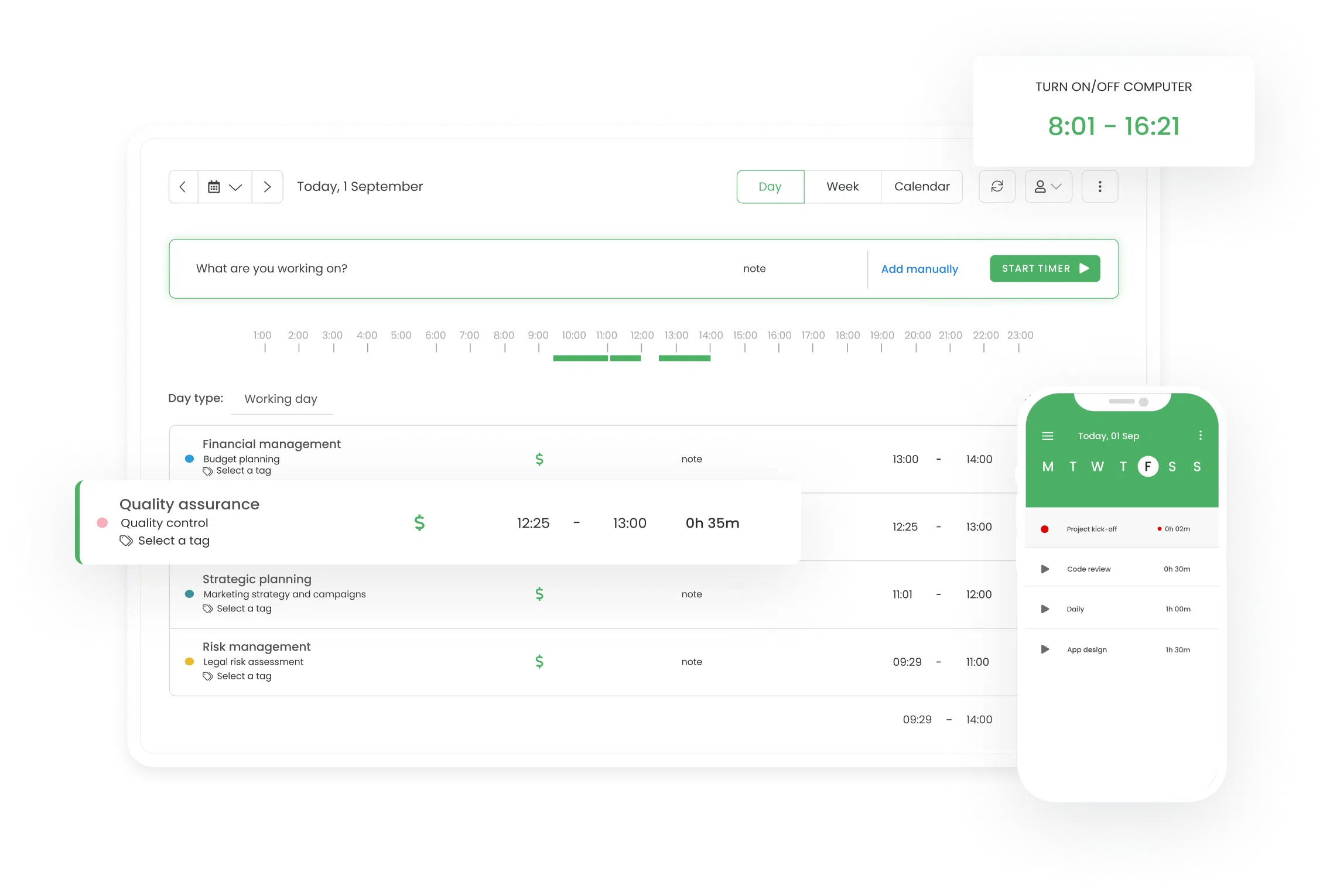
Such a system not only aids in data loss prevention but also gives employees access to user activity logs and user behavior analytics so people can learn they work habits and improve productivity.

3. Better Time Management and Efficiency
In addition to analyzing work patterns, UAM can help managers understand how effectively time is being utilized. For example, it can track how long employees spend on specific tasks or projects, enabling managers to allocate resources more efficiently.
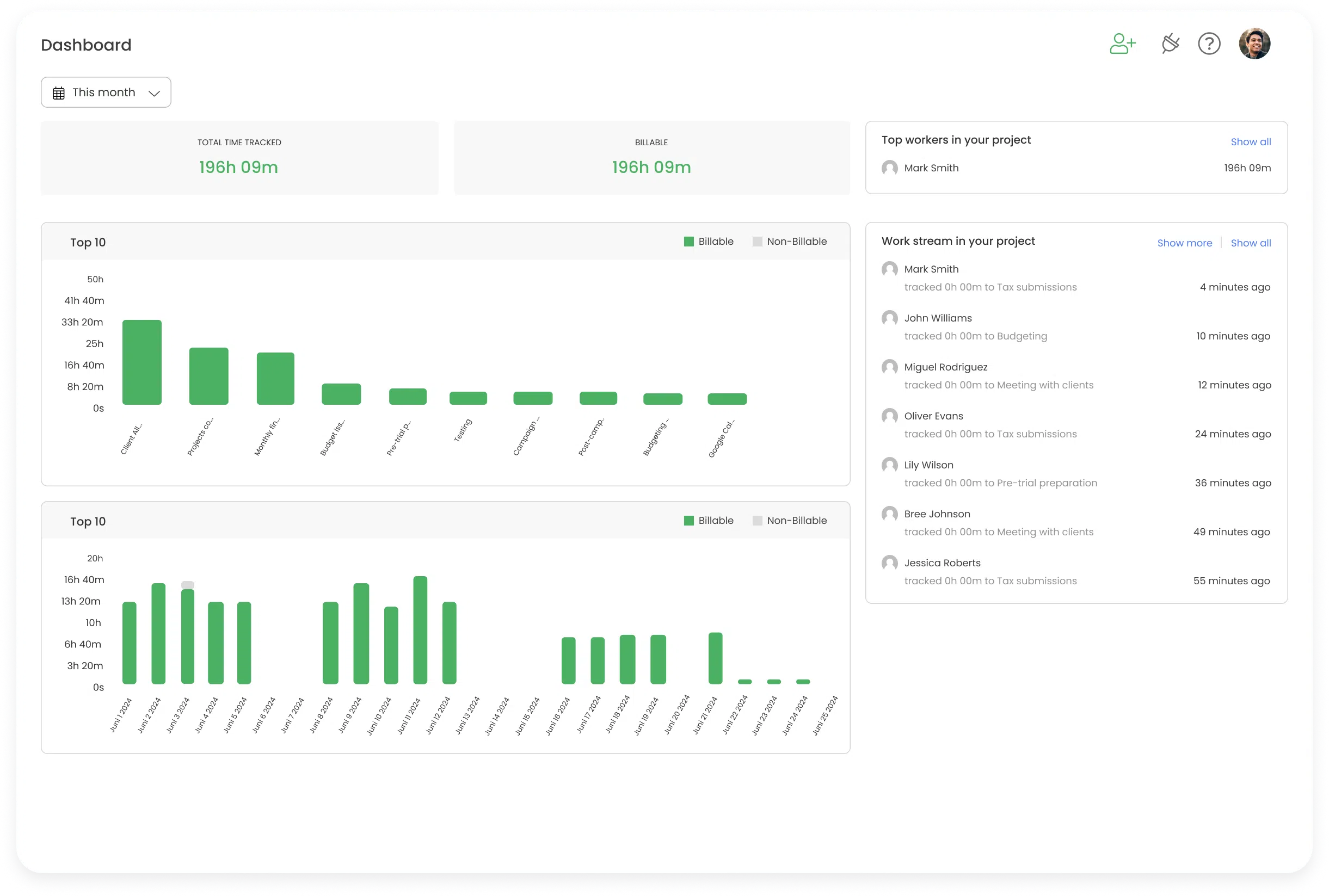
By identifying tasks that consume excessive amounts of time, you can implement strategies to streamline processes, automate repetitive tasks, and ultimately enhance productivity.
4. Compliance and Legal Considerations
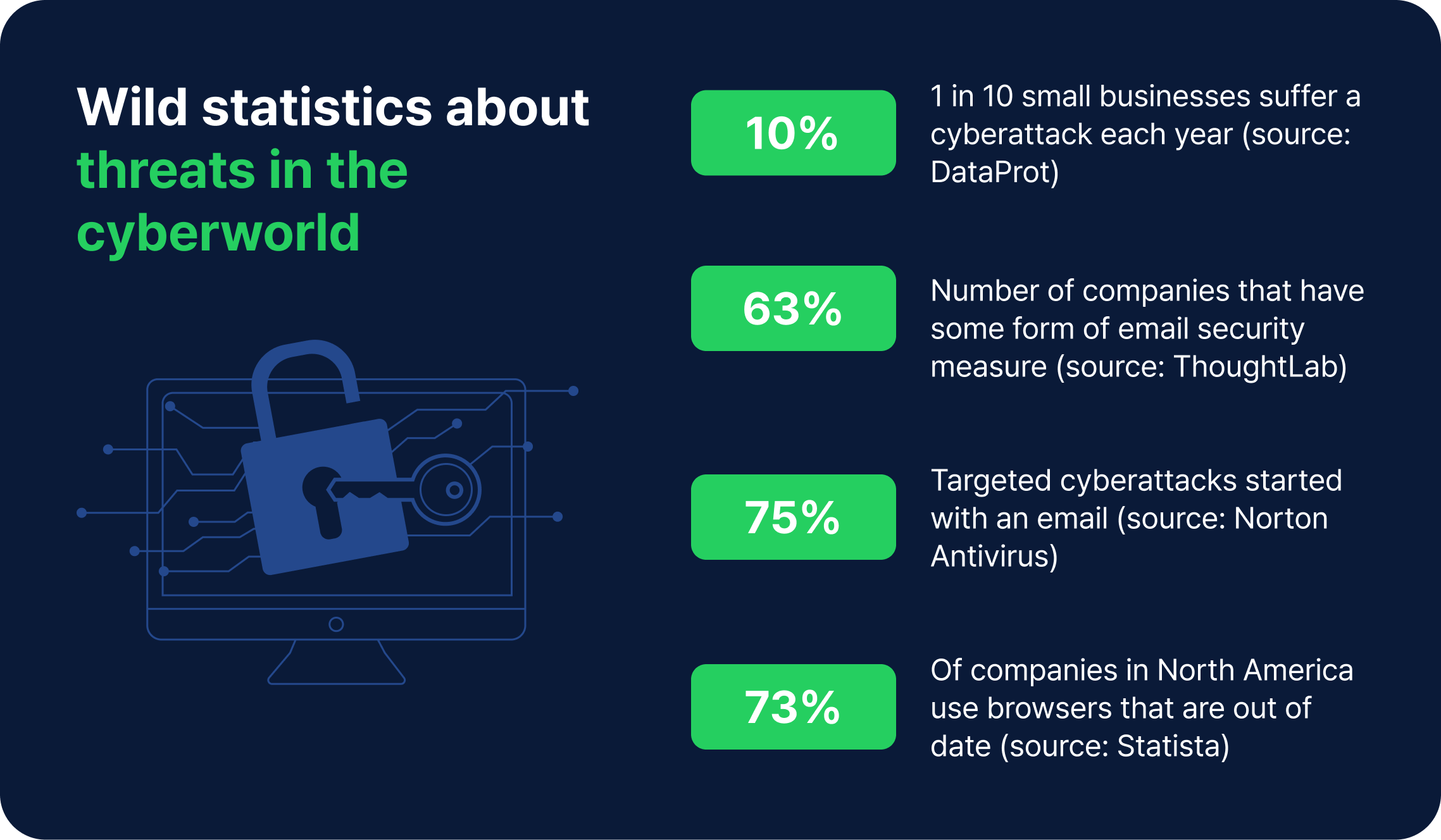
Many industries are subject to strict regulatory requirements regarding data privacy and security. User activity monitoring helps organizations comply with these regulations by providing detailed logs of user activities, which can be used to demonstrate compliance during audits.
For example, healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA), which requires strict controls over patient data. UAM tools can monitor access to this data and ensure that only authorized personnel are handling it.
5. Avoiding Legal Disputes and Fines
Failure to comply with regulatory requirements can result in significant legal and financial penalties. User activity monitoring tools help mitigate these risks by ensuring that user activities are continuously monitored and that any potential compliance violations are flagged and addressed promptly.
It’s a proactive approach that helps you avoid fines but also protects their reputation and builds trust with clients and stakeholders.
6. Facilitating Remote Work
With the rise of remote work, UAM has become an invaluable tool for managing distributed teams. It enables you to monitor the activities of remote employees just as they would in an office setting, ensuring that work is being done efficiently and securely.
TimeCamp helps companies strengthen the sense of transparency and accountability among employees. Additionally, as mentioned many times above, data from our time tracker serves as a reference point for performance reviews, leading to noticeable refinements in workflow. Both are primary concerns holding companies from going remote, and either can be easily addressed with time tracking.
User activity monitoring software can track login times, application usage, and communication patterns, providing managers with the data they need to support remote employees and address any challenges that arise.
But above all, monitoring user activity in remote workforce helps teams to communicate and collaborate better so they can work effectively, no matter where your employees are located.
Ethical and Privacy Considerations: Is It Legal to Monitor Employees?
Employee monitoring is a complex topic that involves various legal and ethical considerations. And it’s difficult to give a precise “yes” or “no” answer.
The legality of monitoring user activity varies by jurisdiction, and it’s important for employers to be aware of the relevant laws and regulations in their specific location.
Federal and State Laws
In general, in the United States, federal and state laws guide the practice of employee monitoring. The U.S. lacks a specific federal statute for employee monitoring and user activity tracking; instead, a mix of federal and state laws, alongside court rulings, guide the practice.
There’s the Electronic Communications Privacy Act (ECPA) that regulates electronic communication interception, permitting employer monitoring under certain conditions like legitimate business purposes or with employee consent.
The Fair Labor Standards Act (FLSA) necessitates precise tracking of work hours for overtime compensation, often facilitated by time-tracking software. If you work in the healthcare sector, the Health Insurance Portability and Accountability Act (HIPAA) mandates the protection of private health information, obliging employers to secure such data.
When it comes to state laws, many states have their own laws regarding employee monitoring, including laws related to electronic communications and wiretapping. As an employer, you must comply with both federal and state laws.
Employee Consent, Privacy Rights, and Union Agreements
In many places, monitoring user activity legally requires employee consent. Employers must clearly communicate the monitoring’s scope and intent through consent forms.
Employees in the United States have certain privacy rights, but these rights are not absolute. Courts often balance an employee’s right to privacy with an employer’s legitimate business interests when determining the legality of monitoring.
You can refer to The National Labor Relations Act (NLRA) that ensures employees’ rights to unionize and discuss work terms freely. Or the Stored Communications Act (SCA) which sets boundaries on employers’ access to employees’ electronic communications stored on company devices or servers. Compliance with the SCA is necessary to respect employees’ privacy rights in the context of workplace monitoring.
International Laws
If you work outside the United States, for example the European Union, there’s the General Data Protection Regulation (GDPR). The GDPR imposes strict requirements on the processing of personal data, including employee data.
For other countries, it’s best to follow national guidelines.
To gather comprehensive information, you can consult legal experts, labor attorneys, and relevant government websites. Additionally, refer to specific state laws and regulations for a complete understanding of the legal landscape regarding employee monitoring in your jurisdiction.
Best Practices for Legal Compliance
A thoughtful and ethical approach is necessary to balance productivity tracking with privacy concerns. There are several actions you can take:
- Create data protection policies: So everyone in your company knows what to expect.
- Stay informed: Regularly review and update policies to reflect changes in laws and regulations.
- Conduct impact assessments: Evaluate the potential impact of UAM on employee privacy and take steps to mitigate any risks.
- Implement data minimization: Collect only the data necessary for legitimate business purposes and avoid excessive monitoring.
- Secure data: Ensure that all collected data is stored securely and access is limited to authorized personnel.
- Set a security event manager: If you deal with a lot of sensitive company data, appoint a person or a security team responsible for data privacy regulations who will maintain security on a professional level.
But above all, always communicate with your team, create an open culture of trust where everyone can share their concerns. And remember that using activity monitoring software should help your employees, not spy on them.
Try best time management app!
Free time tracking & easy attendance, project profitability analysis and precise billing.
Challenges of Implementing User Activity Monitoring
Since implementing user activity monitoring software can be a challenging practice, you can encounter many obstacles. Here are a few of them and how to deal with them:
1. Technical Challenges
Integration with Existing Systems
Implementing user activity monitoring software often requires integrating new monitoring tools with existing IT infrastructure, which can be complex and time-consuming.
This challenge is particularly pronounced in large organizations with diverse systems and outdated software. Ensuring that UAM tools are compatible with existing systems and that data flows seamlessly between them is crucial for effective monitoring.
TimeCamp is an easy-to-use UAM software. it works in the cloud, so no prior installation is required. With over 70 integrations with major productivity apps, you can quickly blend the system into your workflow. For extra safety, TimeCamp can be hosted on your server.
Data Management and Storage
UAM generates large volumes of data, which must be stored securely and managed efficiently. It’s important to establish protocols for data storage so that it’s easily accessible for analysis while also being protected against unauthorized access.
Additionally, define data retention policies to determine how long UAM data is kept and when it should be deleted.
2. Organizational Challenges

Resistance from Employees and Stakeholders
One of the most significant challenges in implementing UAM is resistance from employees and stakeholders. Employees may view monitoring as an invasion of privacy. That can lead to pushback and decreased morale.
Similarly, stakeholders might have concerns about the cost, complexity, and ethical implications of monitoring.
Overcoming this resistance requires clear communication, transparency, and involving employees in the decision-making process.
Managing Change and Adoption
Introducing user activity monitoring software requires a change in organizational culture, which can be difficult to manage. Employees need to be educated on the purpose of monitoring and how it will be implemented.
Change management strategies, such as training sessions, regular updates, and feedback loops, are essential for ensuring a smooth transition and encouraging adoption.
3. Ethical and Legal Risks
Potential for Misuse or Abuse
UAM has the potential for misuse if not implemented and managed correctly. This includes using monitoring data for purposes other than those originally intended, such as unfairly targeting specific employees or invading personal privacy.
To mitigate these risks, it’s best to establish clear policies, conduct regular audits, and ensure that monitoring is conducted ethically and transparently according to the law.
Handling Sensitive Information Responsibly
UAM often involves the collection of sensitive information, such as login credentials, email content, and personal data. Organizations have a responsibility to handle this information with care, ensuring that it is protected against unauthorized access and that employees’ privacy rights are respected.
Implementing strict access controls, encryption, and regular security audits are critical for safeguarding sensitive data.
Best Practices for Effective User Activity Monitoring
It’s difficult to balance the use of activity monitoring tools with employee privacy and sense of safety. There are, however, practices you can implement to help create friendly atmosphere and make your workforce feel secure.
Here are 3 main elements that will make user activity monitoring work in your business:
1) Clear Policy Development
Effective UAM starts with clear and comprehensive policies that outline the purpose, scope, and methods of monitoring. These policies should define what activities will be monitored, how data will be collected and used, and the responsibilities of both employees and management.
Clear policies help set expectations and provide a framework for consistent and fair monitoring practices.
Once you develop user activity tracking policies, communicate them clearly to all employees. This includes not only distributing written policies but also holding training sessions and providing resources to answer any questions employees may have.
Transparent communication ensures that employees understand the reasons for monitoring and how it will affect their daily work.
2) Ensuring Transparency and Trust
Transparency is key to building trust. It’s best to be open about what is being monitored, why it is being monitored, and how the data will be used. You can achieve it through regular communication, such as newsletters, town hall meetings, or dedicated sessions where employees can ask questions and provide feedback.
Beyond transparency, it’s a good idea to foster a culture of trust and accountability. This involves treating employees as partners in the monitoring process, involving them in discussions about UAM practices, and ensuring that monitoring is conducted fairly and respectfully.
When you build a culture of trust, organizations can mitigate potential negative impacts of UAM and enhance overall employee satisfaction.
3) Leveraging User Activity Monitoring Tools Effectively
First of all, selecting the right UAM tools is crucial for effective monitoring. Consider factors such as the specific needs of your industry, the scale of your business operations, and the level of detail required.
Don’t forget about all the important features such as user-friendly and intuitive interface, scalability, real-time monitoring, automated alerts, and detailed reporting.
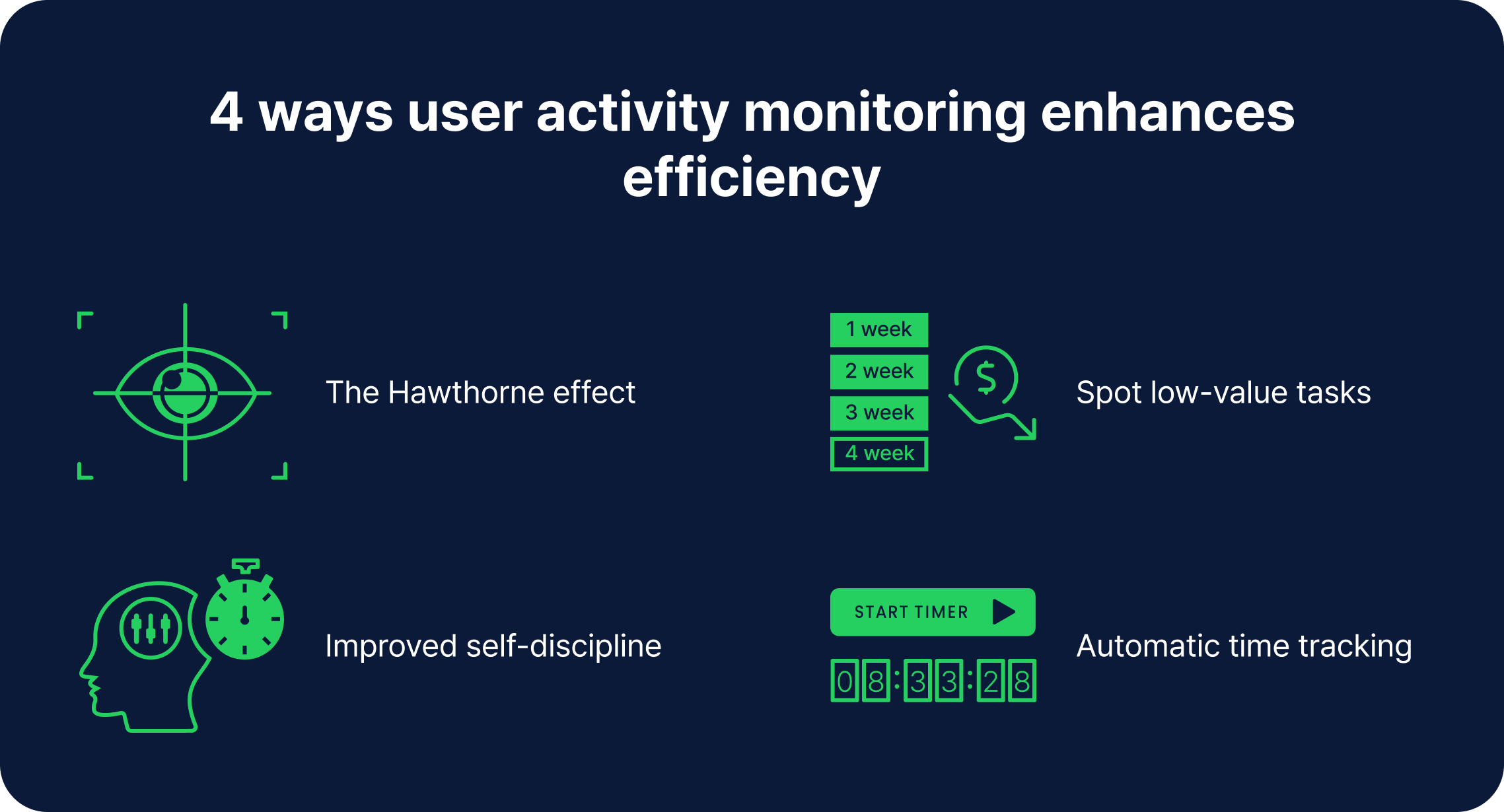
Additionally, to ensure that UAM is effective conduct regular audits and assessments. Check the effectiveness of current monitoring tools, identify any gaps or areas for improvement, and ensure that data is being handled in accordance with policies and legal requirements.
It’ll help you stay proactive and responsive to changes in the monitoring landscape.
Final Thoughts: Mastering UAM for a Secure and Productive Future
As work and technology continue to evolve, the role of UAM is only going to get bigger. Staying in the loop on the latest trends and regulations is key to making sure your UAM practices are on point.
It’s about protecting your organization, respecting your employees, and making sure you’re ready for whatever the future throws your way. Especially with the raise of modern solutions and evolving features such as AI, machine learning, and automation.
How does user activity monitoring work in your company? Let us know in the comments.


